"The myth of cyberspace as a digital utopia has long been put to rest. Governments are increasingly developing smarter ways of asserting their national authority in cyberspace in an effort to control the flow, organization, and ownership of information." "The Hacked World Order" Adam Segal, 2015 from https://www.cfr.org/book/hacked-world-orderPrompted by some struggles of Facebook friend, I have drawn up a quick guide to Computer Security for the Average Politico. The digital world is one big hackfest now. If you are storing or manipulating political data or just blogging on Facebook you are probably subject to attacks, ex-filtration of private data and maybe harassment. Computer security is almost impossible to achieve. We live in a world where American cities like Baltimore are held cyber hostage potentially by exploits stolen from the NSA. Assume there are armies of paid information warriors targeting and collecting information on activists just like you and implementing large scale strategies to discourage, distract, weaken your efforts. Fight back some. Cyber bullies (spies or not) are cowards. I will assume Windows 10 for the discussion below, but my suggestions should be generic and OS independent enough.
Use the advice in this post at your own risk. Remember to back up critical data to a separate device first. Remember the old Unix maxim: "There are two kinds of computer uses: Those who have lost data and those will." For Windows 10, please see information on the 'administrative' or 'elevated' use of cmd.exe and Powershell. This post may need expansion and more explanation. To be updated. - 06/23/2019 RMF
[Best References]
Use Microsoft Safe Computing Tutorials as a reference:
- https://www.microsoft.com/en-us/digital-skills/online-safety-resources
- https://support.microsoft.com/en-us/help/4092060/windows-keep-your-computer-secure-at-home
- https://support.microsoft.com/en-us/help/4092059/windows-keep-your-computer-secure-at-work
Use Google Safe Computing Tutorials as a reference:
[Easy]
- Ruthlessly virus scan your PCs and hosts. For example, use the "Windows Security" applet. If necessary, use Microsoft's "Malicious Software Removal Tool" to scan and clean all your drives. This may take some time and have some risk. I recommend backing up your important data to an external portable hard drive and keep it safe and secure.
- Update and upgrade as instructed: Operating Systems, Web Browsers, other important apps and applications.
- Change your passwords at some interval or when you have been notified your accounts have been hacked or illegally accessed. Recommendations on this vary. Please see Bruce Schneier's comments on password security [1,2].
- Deploy secondary authentication for online sessions. For example 'Google 2 step authentication' @ https://www.google.com/landing/2step/
[Medium Easy]
- Remove little used and unnecessary applications.
- Clean up your storage by removing unneeded files.
- Back up your data to an external portable hard drive and keep it safe and secure.
- Teach yourself performance and task monitoring utilities like Windows 'Task Manager' and 'Resource Monitor'.
- Consider deploying a password manager. See this discussion on the risks and benefits.
- Check Firefox Monitor's database to see if your passwords have been compromised @ https://monitor.firefox.com/. Change passwords as necessary.
[Medium Hard]
- For Windows 10, please see information on the 'administrative' or 'elevated' use of cmd.exe and Powershell.
- Consider updating your drivers from hardware vendors. 'Device Manager' can help you do this in Windows.
- Check the security and content of your online assets regularly.
- Consider advanced log analysis and alerting as a regular habit. For example, learn to use 'Event Viewer" (eventvwr) in Windows.
- Implement router, host, network security. Treat your router as a potential gateway/target.
- Teach yourself administrative skills like Windows "Microsoft Management Console" (mmc.exe) snapins: 'Services', 'Device Manager' and 'Security Configuration and Analysis'.
[Harder But Not Impossible]
- Configure your router's firewall to the greatest level of security need. Deny remote management.
- Make your wireless network name 'hidden' or private so as to not broadcast on from your router. Alternatively use copper instead of wireless.
- Set up logging on your internal and host firewalls. Teach yourself to read and understand firewall logs. Proactively configure those firewalls for security. (This may benefit from some requires TCP/IP skillsets.)
- Use and learn Sysinternals utilities developed by Mark Russinovich for Microsoft including Sysmon, Procmon, and AutoRuns
[Difficult, possibly labor intensive, requires admin access with skills and probably fraught with some risk.]
- For Windows 10, please see information on the 'administrative' or 'elevated' use of cmd.exe and Powershell.
- Run from Windows cmd.exe: 'chkdsk' and 'defrag' at some preferred periodicity. (This is not without a learning curve and risk.)
- Perform network and performance monitoring both locally and on your network. You can use Event Viewer) (eventvwr), Resource Monitor (resmon) and Performance Monitor (perfmon) and Microsoft Message Analyzer: https://www.microsoft.com/en-us/download/details.aspx?id=44226 (These requires TCP/IP and Operating System skillsets.)
- Consider installing on a second hardware platform a paranoid or overly secure OS like OpenBSD or some secure version of Linux you might like. (This is learning intensive).
- Consider installing a packet sniffer like 'Wire Shark' or 'Microsoft Messaging' teaching yourself to read network traffic (This requires TCP/IP skillsets).
- Consider using Virtual Machines inside your OS as a security sandboxes [1, 2].
- Consider using Windows Linux Subsystem tools on Windows 10.
[Advanced Techniques:]
Learn your shell's network utilities. Append "/?" to cmds below. For Windows 10, please see information on the 'administrative' or 'elevated' use of cmd.exe and Powershell:- ipconfig
- ping
- pathping
- route
- netstat
- nbtstat
- net Server
- net Workstation
- nslookup
- 'net' commands
Consider reading and subscribing to security messages from all your vendors:
- Host PCs
- Phones
- Virus and Firewall Vendors
- OS Vendors
- Router and networking equipment vendors
- Hardware Manufactures like Intel and AMD
- External sources like Brian Krebs newsletter
Consider understanding and deploying Windows Event log and Windows Auditing for cmd.exe.
- auditpol
- secedit
- eventvwr
- Microsoft Message Analyzer: https://www.microsoft.com/en-us/download/details.aspx?id=44226
Consider learning about syslogd and syslogging
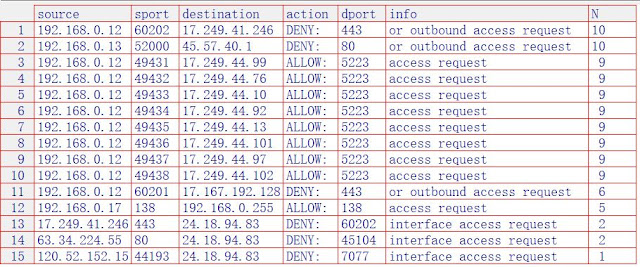
Setting up a syslog daemon or capturing packets forwarded from your router's syslog daemon can tell you a lot about your network. It is a bit beyond the average user, but here is an example of the the type of data a syslog daemon can gather:
Consider installing and running additional security utilities like those described at:
- https://docs.microsoft.com/en-us/sysinternals
- https://www.malwarebytes.com/
- https://www.wireshark.org/
Understand hardware security more completely:
- https://www.intel.com/content/www/us/en/security/hardware/hardware-security-overview.html
- https://www.amd.com/en/technologies/security
No comments:
Post a Comment